Hey there, internet surfers! In today’s digital age, we’re all connected through the World Wide Web. But have you ever wondered how secure our online data is while we’re shopping, chatting, or simply browsing? If you’re a teenager like me or just someone who wants to learn about internet security, you’re in the right place! […]
Introduction: Since the invention of the internet, hackers have been working to find vulnerabilities in computer systems, while cybersecurity professionals have been working to prevent unauthorized access to those systems. This ongoing battle has led to a significant progression in both hacking techniques and cybersecurity practices over the years. In this blog, we’ll explore the […]
Security is a critical aspect of our lives that should never be taken for granted. Whether it is personal security, physical security, cyber security, or any other form of security, it is essential to take necessary measures to ensure your safety and the safety of your assets. In this blog, we will discuss the importance […]
I. Introduction As a CEO or senior executive, you have a lot on your plate. But when it comes to prioritizing what is most important for your company, employees, and shareholders, risk management is consistently a top concern. In this article, we’ll provide a comprehensive guide to enterprise risk management, helping you navigate the complex […]
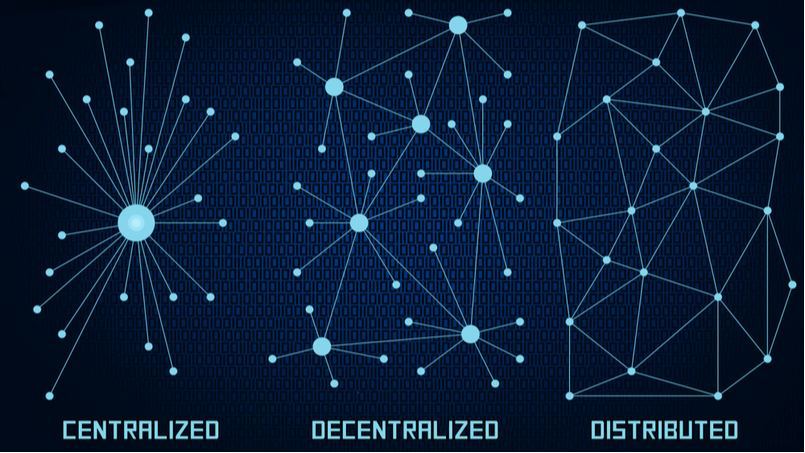
As the internet continues to evolve and expand, it’s become increasingly clear that traditional centralized systems are not equipped to handle the growing demands and challenges of the digital age. From data breaches and censorship to central points of failure and control, the limitations of the current internet infrastructure have become more apparent than ever. […]
The world of antivirus protection has a long and storied history, and few figures loom larger in that history than John McAfee. In 1987, McAfee founded McAfee Associates, a company dedicated to developing software to protect computers from viruses and other malicious threats. At the time, the idea of antivirus software was still relatively new, […]
Introduction to the Metaverse The Importance of a P2P, Decentralized Mesh Network The Role of AI in the Metaverse Conclusion Introduction to the Metaverse The Metaverse is a virtual world that is built on top of the internet, where users can interact with each other and with digital objects and environments in real-time. It is […]
Well there are many attack vectors that cyber criminals can use to acquire access to systems and personal information most of them can be placed into only a few method types. 1. Direct access from brute force attack or DDOS ect (this is when an attacker finds information about your business or personal information online […]
Red Blog First Aid tips that are a Cut above the reat. Travelling and working abroad can be a fantastic opportunity to experience the world and enjoy the lifestyle and Coulter of other locations, however it doesn’t come without risks. We have put together some tips, packing lists and other information to help you prepare […]
If you are self-employed or freelance working with other companies means you are responsible for managing confidential information and documentation from many clients well acting on behalf of the company be it for consulting or sales roles, you have a duty of care and sometimes legal obligation to keep accurate records from the first point […]